
What Is HTTPS?
HTTPS is the main protocol used to send data between a web browser and a website is the hypertext transfer protocol (HTTP). HTTPS uses TLS (transport layer security) to encrypt HTTP requests and responses, making it a secure version (hence the “S”) of the same protocol. It is used in various applications such as account logins, e-commerce, and web mail applications to name a few.
NOTE: TLS certificates are often referred to as TLS/SSL certificates.
How does HTTPS Work? (the basics)
HTTPS is an implementation of TLS encryption on top of the HTTP protocol. Therefore, when a user visits a site that supports HTTPS, they get the following security benefits:
- Authentication: Helps to verify the identity of the website. For example, if the browser bar displays https://www.entrust.com, you can be confident that it is owned by Entrust Corporation.
- Encryption: Hides the data in motion from third parties.
- Integrity: Verifies that the data has not been tampered with.
Why is authentication in HTTPS so important?
Authentication of a website is important because it allows a site visitor to verify the identity and ownership of a website, helping them distinguish between a real website and a potentially fake or fraudulent website.
A site visitor can end up on an incorrect website through various attack vectors such as DNS poisoning, malware, or phishing sites.
Associating an identity with a website is typically carried out by a third-party organization such as a certificate authority (CA) that follows strict industry guidelines.
How does identity in HTTPS work?
A web browser that connects to a website will make use of a TLS/SSL certificate issued by a certificate authority such as Entrust to authenticate to an HTTPS website.
Requesting a TLS/SSL certificate
To add identity to a website, a TLS/SSL certificate must be requested by a website owner and issued by a publicly trusted certificate authority such as Entrust. A TLS/SSL certificate is analogous to a digital passport for a business as it includes verified details such as:
- Website URL(s)
- The organization that own’s the website
- The issuance and expiration dates of the certificate
- The name of the certificate authority that issued the certificate
- The public key (used for encrypting data)
To obtain a TLS/SSL certificate, a website owner must go through the following steps:
- Generate a certificate signing request (CSR), which includes a public/private key pair
- Demonstrate to the certificate authority that they control the domains to be included in the TLS/SSL certificate
- Prove the identity of the organization and that they are authorized to request a TLS/SSL certificate on behalf of the organization
After the verification process is completed, the TLS/SSL certificate is issued and can then be installed by the website owner on the appropriate sites. The TLS/SSL certificate is then presented every time a site visitor connects to a website URL via https://
How a website shares its identity with site visitors
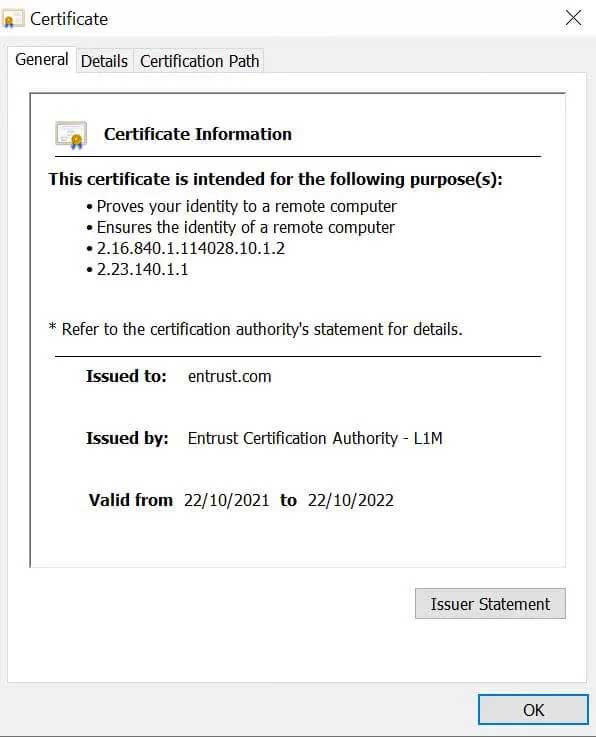
When a site visitor goes to an HTTPS website, their web browser is sent a copy of the TLS/SSL certificate. Clicking on the padlock icon on the left of the URL bar, then selecting Connection is secure and Certificate is valid will display a website certificate similar to the image below.
A site visitor can open the Details tab to view more information about the organization that owns the website, similar to the image below.
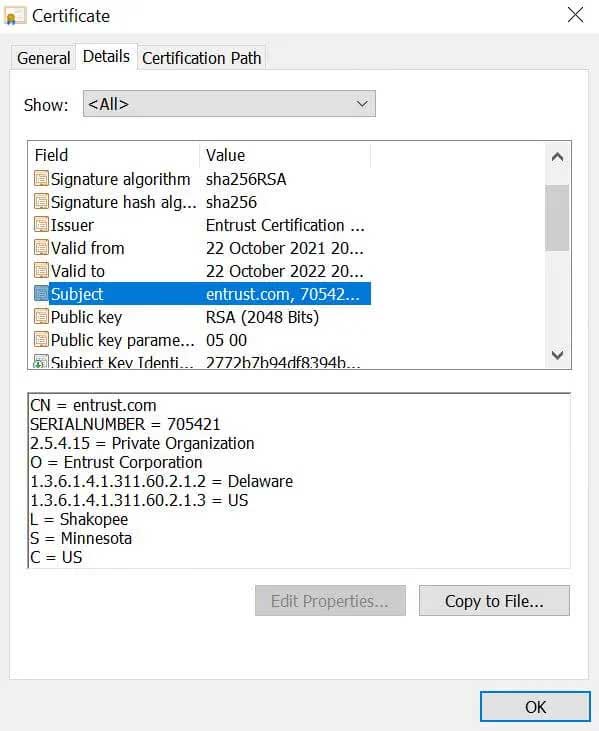
SSL certificate details for entrust.com
If the certificate shows the website owner’s company details (company name, location), it is either an extended validation (EV) or organization validation (OV) certificate.
How a browser verifies a TLS/SSL certificate
A browser will carry out a sequence of checks to verify that the TLS/SSL certificate presented by the website is accurate and legitimate. The browser will:
- Check the digital signature of the certificate authority to verify that the certificate was issued by a certificate authority on the browser’s trusted root store
- Verify that the domain in the SSL certificate matches the domain of the website that the site visitor is accessing
- Verify that the SSL certificate is valid and has not expired or been revoked
After completing these checks, the site visitor’s browser will display https:// and a padlock icon in front of the website URL.
The image below shows that the website’s certificate was issued by Entrust, and that it includes a digital signature from Entrust that the site visitor’s browser can use to verify that the certificate is valid and issued by Entrust.
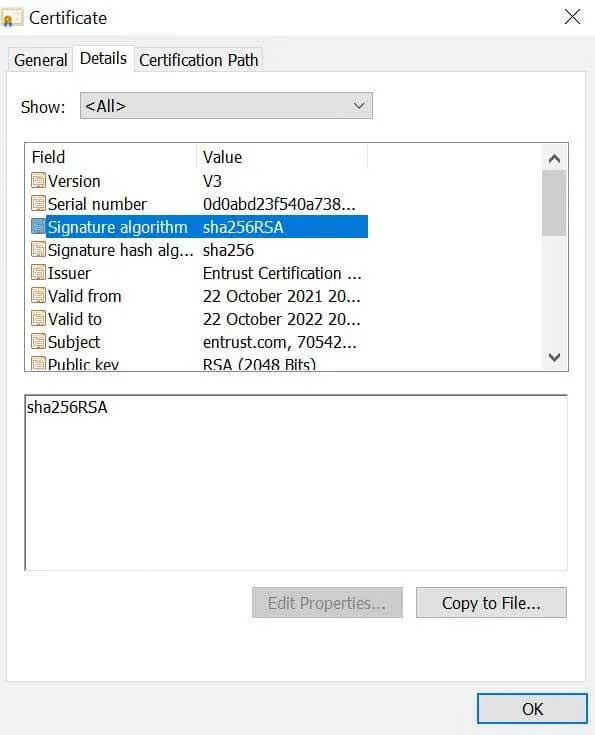
Digital signature on an SSL certificate issued by the Entrust Certification Authority
Root stores
In order to verify a website’s TLS/SSL certificate, a browser needs a copy of the certificate authority’s public key, which is stored in a browser’s root store.
A root store contains the digital certificates and associated public keys of every certificate authority that it trusts.
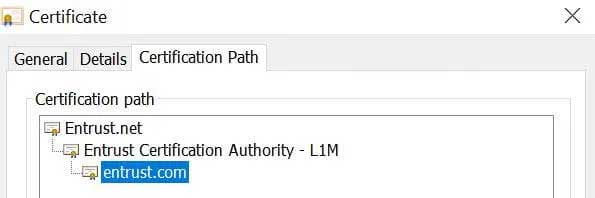
Certification path for Entrust.com’s SSL certificate
- The top certificate is the root certificate. It is pre-loaded in the browser’s root store.
- The middle certificate is the intermediate certificate. It is digitally signed by the root certificate CA and therefore the browser will also trust it. The browser verifies the signature using Entrust’s public key from the pre-loaded root certificate.
- The bottom certificate is the end entity certificate and is Entrust’s TLS/SSL certificate sent by the web server when the browser connected to the site. The browser can verify the end entity certificate by using the intermediate certificate’s digital signature.
How does encryption in HTTPS work?
On any HTTPS website where a site visitor enters information (credit card details, login details, fills out a form, etc.) before the data is sent from the browser to the server, the browser will encrypt the data using the public key from the website’s TLS/SSL certificate.
The encryption process is a way to scramble the data in transit so it can only be read by authorized parties. Encryption, therefore, translates human readable plain text into unintelligible ciphertext.
Encryption appears to make the data look random, however encrypted data follows a logical and predictable pattern. But it is necessary for the website receiving the data to have the right private key to decrypt the data.
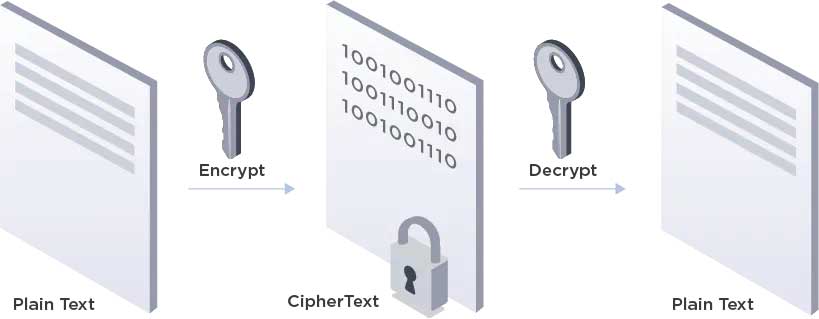
High-level overview of the encryption and decryption process
What is a key in cryptography?
A cryptographic key is a string of characters used within an encryption algorithm to alter the plain text data so that it appears random. The cryptographic key is used to encrypt and decrypt the data.
What are the different types of encryption?
There are two main types of encryption:
Symmetric encryption
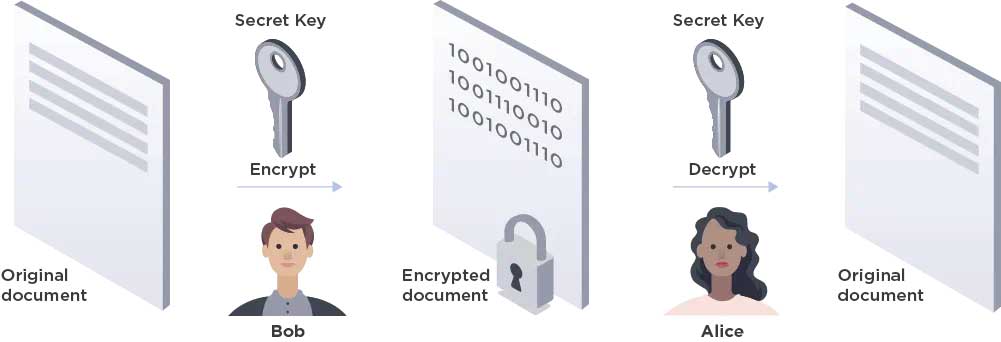
Symmetric encryption includes only one key, which is used and shared among all communicating parties to both encrypt and decrypt the communication. While symmetric encryption is faster than asymmetric encryption, it is not a scalable form of encryption due to complexities associated with the secure distribution of the key.
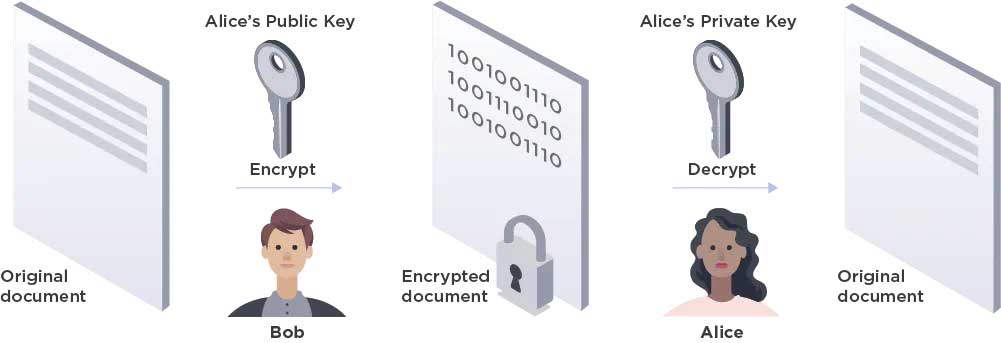
Asymmetric encryption
Asymmetric encryption (also known as public key encryption) includes two separate keys. One key (the public key) is accessible to anyone and is used for encryption. A second key (the private key) is kept secure by the recipient and is used for decryption. Asymmetric encryption is slower than symmetric encryption, but distribution of the keys across multiple users is easier.
What is an encryption algorithm?
An encryption algorithm is the method that converts plain text into ciphertext. Plain text is converted into ciphertext when an encryption algorithm alters the data in a predictable way by using a private key. This allows the ciphertext to be converted back into plaintext by using a decryption key.
Popular symmetric encryption algorithms are:
- AES
- 3-DES
- SNOW
Popular asymmetric encryption algorithms are:
- RSA
- Elliptic curve cryptography (ECC)
What is the TLS/SSL handshake?
A TLS connection is started by following a sequence often referred to as the TLS/SSL handshake. This process is started when a website visitor opens a website that uses a TLS/SSL certificate. The process begins between the user’s device and the website they are connecting to.
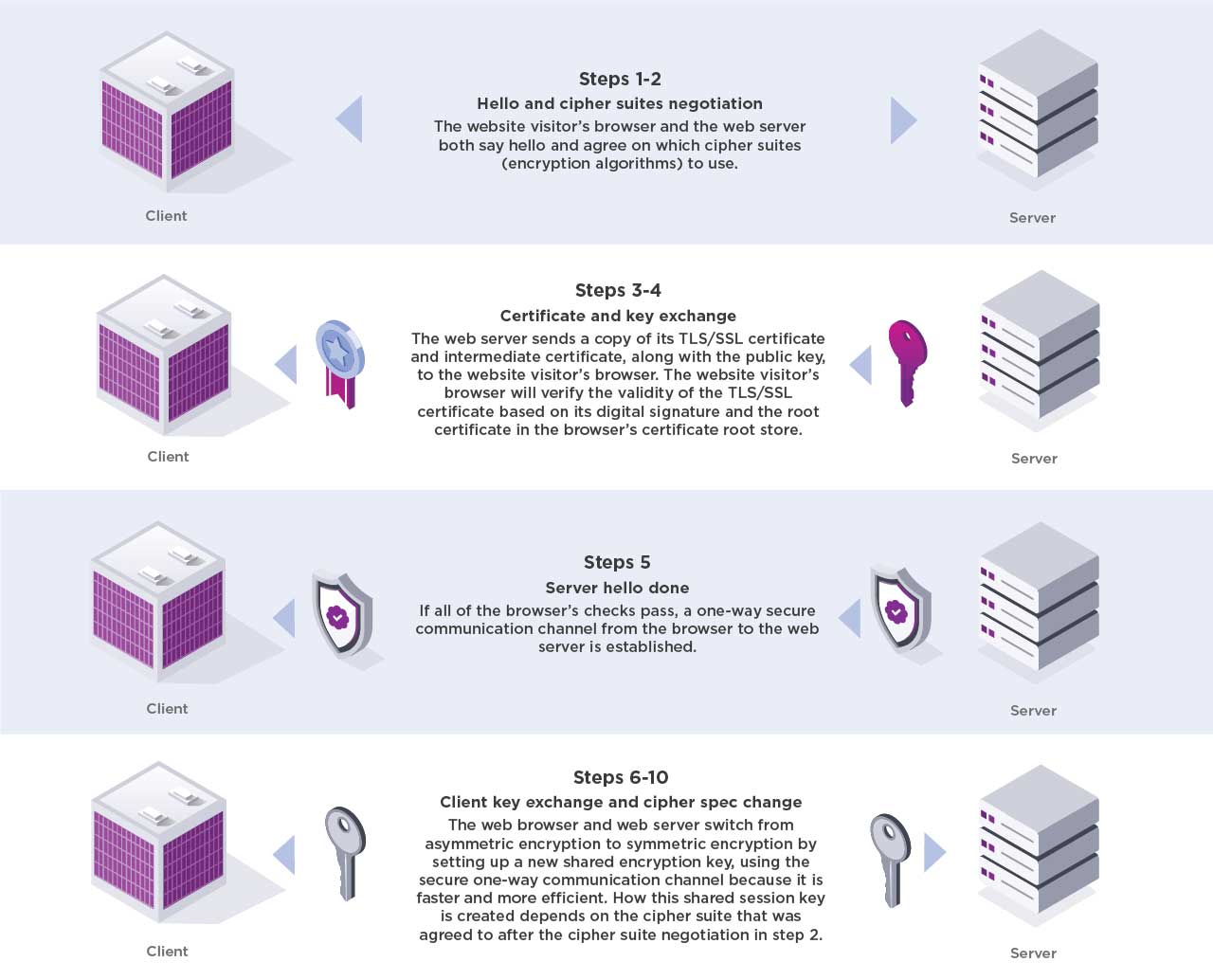
Steps 1-2: Hello and cipher suites negotiation
The website visitor’s browser and the web server both say hello and agree on which cipher suites (encryption algorithms) to use.
Steps 3-4: Certificate and key exchange
The web server sends a copy of its TLS/SSL certificate and intermediate certificate, along with the public key, to the website visitor’s browser. The website visitor’s browser will verify the validity of the TLS/SSL certificate based on its digital signature and the root certificate in the browser’s certificate root store.
Step 5: Server hello done
If all of the browser’s checks pass, a one-way secure communication channel from the browser to the web server is established.
Steps 6-10: Client key exchange and cipher spec change
The web browser and web server switch from asymmetric encryption to symmetric encryption by setting up a new shared encryption key, using the secure one-way communication channel because it is faster and more efficient. How this shared session key is created depends on the cipher suite that was agreed to after the cipher suite negotiation in step 2.
After the session key is generated, the TLS handshake process is completed and the web browser and the web server use the session key to encrypt and decrypt all of the data that is exchanged.
